Bletchley Park
The Estate
Except from interview with Dr. Duncan Anderson, head of the
Department of War Studies at Sandhurst Academy
|
|
|
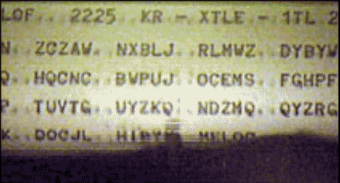
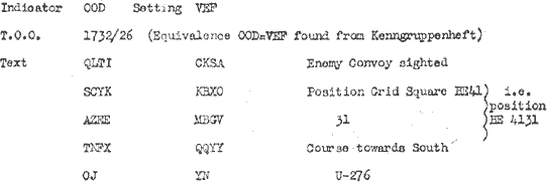
Decryption
Glossary Page 1
Glossary Page 2
Ultra
"The secret British program to monitor and decipher Germany's Enigma signals"
- Sir Lawrence David Freedman, Professor of War Studies, King's College London
Enigma
“Three rotors, side by side, created an electrical maze. As they turned, they changed the maze - and thereby the encipherment. The result was a rather secure cipher”
- Dr. David Kahn, leading historian
Bletchley Park
“Bletchley Park was concentrated on deciphering, translating, evaluating and distributing the vast amount of information...transmitted by the Germans after they had been rendered 'secure' by encipherment on the famous Enigma machine”
- Ronald Lewin, British military historian
GCHQ
"After the war, it took over from the Government Code and Cipher School the function of receiving and decoding intercepted wireless traffic from listening stations scattered throughout the United Kingdom and from several dozen overseas"
- Lord Jonathan Sumption, British judge, author and medieval historian
Double Cross System
"For the duration of the war, brilliantly orchestrated false reports sent back to Germany by Masterman's tame agents would lead the German high command into one blunder after another at the most crucial junctures - ensuring the success of the Allied landing at Normandy, helping to turn the tide in the war against U-boats in the Atlantic, even tricking the Germans into firing most of their V-2 rockets short of central London"
- Stephen Budiansky, former national security correspondent, foreign editor, and deputy editor of U.S. News & World Report
Communications Intelligence (COMINT)
"COMINT is technical and intelligence information derived from foreign
communications by other than the intended recipients"
- Department of Defense Directive, 2010
Signals Intelligence (SIGINT)
"Intelligence obtained through the interception of transmission signals"
- Merriam Webster Dictionary
Public Key Encryption
“A standard analogy for public-key cryptography is given as follows. Suppose that Bob has a wall safe with a secret combination lock known only to him and the safe is left open and made available to passers-by. Then anyone, including Alice, can put messages in the safe and lock it. However, only Bob can retrieve the message, since even Alice, who left a message in the box, has a way of retrieving the message.”
- Richard A. Mollin, author and professor